Expanding WeBaCoo
 After two months from the initial release, WeBaCoo core communication functions are stable enough to provide a strong base for building some expansion modules. These modules are nothing more than regular actions that pentesters and sysadmins execute while interacting with the system, including database interactions, data file manipulation and more. The concept behind extension modules development, is to provide stealth, stable and highly customizable functionalities within the main terminal mode to assist users. All modules operate under the main WeBaCoo communication function and customize some settings in the target system if it is necessary for the module’s operations.
After two months from the initial release, WeBaCoo core communication functions are stable enough to provide a strong base for building some expansion modules. These modules are nothing more than regular actions that pentesters and sysadmins execute while interacting with the system, including database interactions, data file manipulation and more. The concept behind extension modules development, is to provide stealth, stable and highly customizable functionalities within the main terminal mode to assist users. All modules operate under the main WeBaCoo communication function and customize some settings in the target system if it is necessary for the module’s operations.
The extension modules were designed keeping in mind both simplicity and stealth behavior. An extension module that offers large scale functionalities but is capable to expose WeBaCoo by triggering IDS/IPS or application firewalls is not an option. Highly customization levels is an additional goal on the top of the module design hierarchy. The basic module parameters can be given by the user during the module load process within the interaction terminal. Although, experienced users that need to customize some extra parameters can dig into the module’s source code and edit the desired variables as needed. Besides, pentesters preserve a good rumor for their custom tweaking behavior when messing around with open source tools.
For detailed documentation about available extension modules, you can refer to the modules project wiki page.
During the rest of the post three extension modules will be analyzed: mysql-cli, psql-cli and upload.
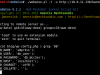
MySQL-CLI
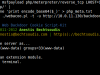
MySQL-CLI was the first module that was developed. It uses the mysql command line utility on the target server to execute mysql commands at the database service (local or remote). When the user loads the mysql-cli module the login credentials are stored in internal variables. During the mysql-cli interaction console, every user given command is packed as an oneliner and executed at the target server returning the relevant output from the database.
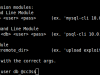
PSQL-CLI
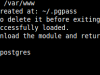
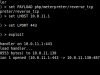
PSQL-CLI is a module to interact with postgres databases. It uses the target system’s psql command line tool to communicate with postgres databases. The challenge while designing this module was to overcome the authentication interaction process that psql tool uses to login. Unlike mysql tool, psql doesn’t offer a password parameter to avoid the password authentication processes. To overcome this, a .pgpass file is created to the user’s home directory with the login credentials.
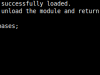
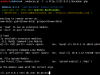
Upload
Messing around with the offered choices and after many tests, the final decision for the upload module was to use the HTTP POST method to upload files to the target host. A tiny php upload code is temporally placed at the target to serve the upload and then it is deleted. Every local file is uploaded as txt/plaintext to avoid any server side limitations or triggering any protection mechanism. Random strings names are generated to enhance the stealth behavior. When using the upload module it is strongly advised to encrypt or obfuscate the files before upload, to prevent any rule based detection for dangerous system/function names.
If you have any further ideas for additional modules contact me.
A. Bechtsoudis