SNMP-BCC — Relay-ing on SNMP for backdoor channel
 Lately I’m working on an SNMP reflection toolkit to study the effects and impact ratio of SNMP Reflection DoS Attacks. During the development phase I spotted some interesting features at the Request-Reply SNMP working model. More specifically, I noticed that if you send an invalid SNMP OID at a GetRequest message the agent replies with a Response message including an error code and the same invalid OID, as specified in the relevant RFCs. SNMP-BCC (Backdoor Communication Channel) takes advantage of the above SNMP feature combined with IP source spoofing techniques, in order to create a stealth communication channel using the SNMP agent as a relay.
Lately I’m working on an SNMP reflection toolkit to study the effects and impact ratio of SNMP Reflection DoS Attacks. During the development phase I spotted some interesting features at the Request-Reply SNMP working model. More specifically, I noticed that if you send an invalid SNMP OID at a GetRequest message the agent replies with a Response message including an error code and the same invalid OID, as specified in the relevant RFCs. SNMP-BCC (Backdoor Communication Channel) takes advantage of the above SNMP feature combined with IP source spoofing techniques, in order to create a stealth communication channel using the SNMP agent as a relay.
SNMP (Simple Network Management Protocol) is a UDP based protocol used mainly for monitor purposes. Its connectionless UDP nature makes SNMP exposed to IP source spoofing attacks. Although, this does not seem to concern network and system administrators as my pen-test cases reveal. The reason that usually (although wrongly) admins do not bother to secure their agents is the read-only behavior. While SNMP offers both read (get info) and write (set configuration variables) under most infrastructures only the read behavior is implemented serving monitor purposes. This creates a belief to admins that there are not any undergoing security risks shifting the problem to anti-spoofing mechanisms.
While messing around with SNMP functionalities the idea for developing SNMP-BCC was born as a PoC to the above wrong approach of the SNMP setups. SNMP-BCC is capable to create a stealth backdoor communication channel with an “owned” host using an SNMP agent as a relay. Initially the desired to sent data are packed following the ASN.1 OID prototype in an SNMP GetRequest packet. Then the source IP address of the UDP packet is altered to the end client’s IP address. This source spoofed packet is transmitted to the public SNMP agent (community string must be known). Of course the SNMP agent can not locate this invalid OID and replies with an error response for the given OID. This error response containing the unattached initial packed data is finally transferred to the end host. Then the client with the relevant decoder can parse the data.
SNMP-BCC is mainly a post exploitation tool that a pen-tester can use to establish a stealth and hard to detect communication channel with a compromised host. Despite the backdoor communcation purposes someone can use the tool for data leakage and node pivoting purposes. While writing this post, the whole project is in its early stage and I haven’t yet decided if it is worth continuing and if so the working model. Although, I developed and made public SNMP-BCC in order to have feedback from my colleagues and infosec community for the next steps.
SNMP-BCC is written in perl using the raw-sockets library and is available at Github under GPLv3 license. Using ‘snmpbcc.pl’ users can create spoofed SNMP packets with system commands under a user interactive pseudo shell mode. For testing purposes the project also includes the ‘backdoor.pl‘ file that serves as a listener in the end host client. I haven’t implemented a fully ASN.1 decoder at the backdoor code, that’s why the command is wrapped with some special characters (‘#$#’) in order to be easily obtained from the response message.
You can get the latest version of the tool by cloning the repository
git clone git://github.com/anestisb/SNMP-BCC.git |
Or by directly downloading the zip project archive
https://github.com/anestisb/SNMP-BCC/zipball/master |
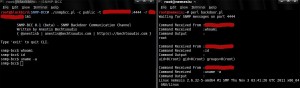
Here is a screenshot with SNMP-BCC in action:
Your comments are greatly appreciated for tool’s evolution.
A. Bechtsoudis


very cool i for one love to use snmp during a pentest it is the most overlooked and sometimes the most valuble foothold considering if you use the right tools you go undetected and dump active tcp and udp open ports and their source and endpoint addresses it is a very powerful pentest tool keep going i had an idea once to make a tool that would dump the username OID from a windows domain controller or windows box and use it to create an rdp session and use the usernames to attempt to bruteforce the rdp protocol which i have done in c# if you would like to see some of the code i made let me know at tech_support@realityrepair.org
i just had an issue with the snmp part
Your bruteforcer idea is cool and can stand as a good start point to work with your preferred SNMP libraries. My philosophy is not to mess different stages during a pentest. Usually i don’t use tools that automate an enumeration/exploitation procedure. I prefer to keep the stages separated having full control during the process.
my question is if i want to dum the entire oid how do i go about dumping just one oid
To dump the entire OID tree just (snmp)walk all of it using GetNextRequest.
Here is a usefull tutorial.
thanks a bunch i thought it was the get next i was dumping the results to a rich text box on the form and than i was going to iterate each one and do the login with the rdp
do you have an email where we could chat id like to show you my code and see if it is corect
Contact details are available on the Contact me page.
i have the tool in progress right now here is a screen shot of it
http://i48.tinypic.com/2vv9a55.png