Enumerating Metadata: Part1 jpeg files
 During the information gathering and reconnaissance phases potential intruders spend a great deal of time learning everything they can about their targets before they launch an attack. The gathered information is often crucial in order to find a weakness in a system or network and users participating in them. Hackers can gather useful information by examining the Metadata (data about data) content of files that are used by the victim user, system or network. In a try to enumerate all the possible Metadata leakage cases, i will write a series of articles covering different filetypes & file groups. In the first part i examine the exif jpeg metadata and how to handle them.
During the information gathering and reconnaissance phases potential intruders spend a great deal of time learning everything they can about their targets before they launch an attack. The gathered information is often crucial in order to find a weakness in a system or network and users participating in them. Hackers can gather useful information by examining the Metadata (data about data) content of files that are used by the victim user, system or network. In a try to enumerate all the possible Metadata leakage cases, i will write a series of articles covering different filetypes & file groups. In the first part i examine the exif jpeg metadata and how to handle them.
When you take a picture with your cell phone, digital camera & other relative devices, there is a lot more information than just the picture that is stored in the file. Depending on the device you use the metadata information stored may include:
- Time and date picture was taken
- Camera make and model
- Integral low-res Exif thumbnail
- Shutter speed
- Camera F-stop number
- Flash used (yes/no)
- Distance camera was focused at
- Focal length and calculate 35 mm equivalent focal length
- Image resolution
- GPS info (if device is not configured properly)
- IPTC header
- XMP data
Spying users and hackers may take advantage of this kind of information in order to create a starting point for their malicious activities. For example using the GPS info and the type of camera you have, the attacker may create a targeted promotional malicious email in order to compromise your system. Or third persons can gather information about you (vacation places & time, place living etc) through the images you have published in social networks & blogs.
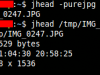
There exist a lot of tools that are capable of reading/altering & removing the jpeg metatada information. In this article i will use a cross-platform tool named jhead and run it under a linux environment.
Download jhead source code (or binary) from the official site and compile using the make file (ignore compiling if you download a binary). Now lets see an example output:
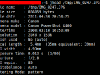
$jhead /tmp/IMG_0247.JPG File name : /tmp/IMG_0247.JPG File size : 866859 bytes File date : 2008:03:10 22:48:36 Camera make : Canon Camera model : Canon PowerShot A460 Date/Time : 2008:03:10 16:53:09 Resolution : 2048 x 1536 Flash used : No (auto) Focal length : 5.4mm (35mm equivalent: 39mm) CCD width : 4.93mm Exposure time: 0.013 s (1/80) Aperture : f/2.8 ISO equiv. : 80 Whitebalance : Auto Metering Mode: pattern |
You can see that metadata information can be gathered pretty easily. In the worst case scenario you may have a GPS location leakage as seen in the screenshots at the end of the post.
Now let’s see how can we prevent this kind of leakage by removing metadata information. In the simplest scenario we can remove all metadata information using jhead. This can be done with the purejpg argument:
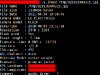
$jhead -purejpg /tmp/IMG_0247.JPG |
Resulting in:
$jhead /tmp/IMG_0247.JPG File name : /tmp/IMG_0247.JPG File size : 857529 bytes File date : 2011:04:30 20:58:25 Resolution : 2048 x 1536 |
Jhead offers a lot more options in order make more advanced changes in jpeg headers, including comment insertion, date & time changes, thumbnail changes, copy exif header from other image and more. Type -h to see the available options or read the official documentation. Additionally jhead can operate on a directory too, making mass changes to all jpeg files in that directory.
And some execution screenshots:
To be continued…..
A. Bechtsoudis


[...] metadata information included in different file types. I recently published the first part about exif jpeg metadata and I will continue with details and tools for others [...]