skipfish: Web Security Reconnaissance Tool
 Skipfish is a fully automated, active web application security reconnaissance tool released by Michal Zalewski (lcamtuf) . Web developers and security professionals can use skipfish to run a series of tests to websites that are under their responsibility. Skipfish support Linux, FreeBSD, MacOS X, and Windows (Cygwin) environments (i have made my tests under Debian distribution). The tool has been released to the public by Google, in order to offer an easy to use and high speed solution for making websites safer.
Skipfish is a fully automated, active web application security reconnaissance tool released by Michal Zalewski (lcamtuf) . Web developers and security professionals can use skipfish to run a series of tests to websites that are under their responsibility. Skipfish support Linux, FreeBSD, MacOS X, and Windows (Cygwin) environments (i have made my tests under Debian distribution). The tool has been released to the public by Google, in order to offer an easy to use and high speed solution for making websites safer.
Skipfish classifies the discovered risks as high, medium and low. Some of the higher risk ones include:
- Server-side SQL injection (including blind vectors, numerical parameters).
- Explicit SQL-like syntax in GET or POST parameters.
- Server-side shell command injection (including blind vectors).
- Server-side XML / XPath injection (including blind vectors).
- Format string vulnerabilities.
- Integer overflow vulnerabilities.
Skipfish isn’t the only available solution. There exist many free and commercial web scanner vulnerabilities tools (like Nikto2 and Nessus), which sometime have better analysis results. In any case, it’s about time people started taking security seriously, and using a tool like this is a good initial step in the right direction.
Let’s proceed to the installation steps:
- Download skipfish from the official site.
- Check downloaded sha1sum with the one from the official site.
$sha1sum skipfish-1.x.tgz
- Ensure that your system meet the requirements (if not install the require packages through your OS package manager):
- libidn11
- libidn11-dev
- libssl-dev
- zlib1g-dev
- gcc
- make
- libc6
- libc6-dev
- Extract files.
- run make to compile the sources. In case of problem read known issues wiki.
After compile has finished, you are strongly advised to read the README-FIRST file, in order to choose the appropriate type of dictionary. As a start if your website application is small, you can use the complete.wl dictionary.
Let’s proceed to the running part.
- In the skipfish main directory make a copy of the complete dictionary
- Create a directory for the output reports.
- Execute skipfish giving the website url.
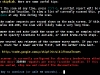
- Hit a key to start the scan.
- Wait the scan to finish. In case you terminate the scanning process you can see the so far reported risks.
- Open the index.html report with firefox.
$cp dictionaries/complete.wl skipfish.wl |
$./skipfish -o outputresults http://example.com |
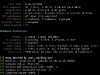
You should then be able to interpret the results easily. Most of the scan results are pretty self-explanatory. It is recommended to pay attention first to high risk vulnerabilities detected by the scan. You can expand those results to read more details.
What to do next? Well you need to educate yourself at understanding and correcting these vulnerabilities, for example if Skipfish is reporting some MySQL injection vulnerabilities in your website you might need to read and learn more about SQL injection. You can use Google to read more details about that vulnerability.
Here are some screenshots from the tool:
Useful links:
- Skipfish documentation
- Understanding and using skipfish
A. Bechtsoudis


skipfish-1.94b released. Download from official website